Hyvä Theme is Now Open Source: What This Means for Magento Community - Mageplaza
Hyvä is now Open Source and free. Discover what changed, what remains commercial, how it impacts the Magento ecosystem, and how to maximize its full potential.
Vinh Jacker | 07-18-2023

Websites are the cornerstone of a business, organization, or person’s online presence in the digital era. However, because of their widespread use, websites have become top targets for hackers looking to compromise security and access confidential data.
A website security audit entails assessing a website’s infrastructure, security methods and controls to spot any potential flaws or vulnerabilities. These audits assess a website’s security measures to uncover and fix vulnerabilities, thus averting potential data breaches and preserving the site’s integrity.
This brief explores the significance of security audits, common vulnerabilities, and strategies for conducting effective audits, empowering website owners to protect their online presence and user trust.
A website security audit evaluates a website’s infrastructure, security processes, and controls to spot any potential flaws or vulnerabilities. It entails thoroughly examining and analyzing numerous elements, including a website’s code, configurations, databases, server settings, and network architecture.
A website security audit’s main objectives are to assess how well the website’s security safeguards are working and find any vulnerabilities that bad actors could exploit. Website owners and administrators can actively identify and fix security problems by conducting routine audits, which lowers the chance of data breaches, illegal access, defacement, or other cyberattacks.

In order to evaluate the security posture of a website, security experts or auditors frequently use a combination of automated technologies and human procedures. They might perform vulnerability scans, penetration tests, code reviews, and configuration reviews to find gaps in the website’s security. They may also check if the website complies with applicable regulatory requirements, industry best practices, and security standards.
A thorough report detailing the discovered vulnerabilities, their seriousness, and suggested fixes is produced after the audit is finished. This paper provides a roadmap for website administrators and owners to prioritize and implement security upgrades to safeguard their website and user data.
In general, a website security audit is an essential preventative strategy to guarantee a website’s continued security and integrity, helping to secure sensitive data, uphold user confidence, and minimize the potential hazards connected with cyber threats.

There are 3 main types of security audits nowadays. The following types of security audits provide valuable insights into the security posture of a website, identifying vulnerabilities, threats, and compliance gaps:
A proactive method to security audits called “threat modeling” entails carefully identifying and assessing potential threats and vulnerabilities that could impact a website. It usually happens during a website or application’s planning and creation phases. The procedure entails the following:
Identifying resources: identifying the essential assets that require protection, such as confidential information, user data, or intellectual property.
Recognizing threats: Recognizing potential dangers, such as internal threats like insider threats or data leaks, as well as external threats like denial-of-service attacks, malware, and hackers. Implementing tools to block malware can mitigate a significant portion of these external threats.
Assessing risks: Judging the probability and probable consequences of each recognized hazard allows organizations to prioritize their security efforts.
Vulnerability assessments are thorough examinations of a website’s security posture to locate holes and known vulnerabilities. Organizations can prioritize vulnerabilities based on their potential impact and take the necessary steps to mitigate the risks by using vulnerability assessments to better understand their websites’ security shortcomings.
An updated and secure website must undergo regular vulnerability audits. Typically, this kind of audit entails the following:
Scanning and testing: Vulnerability assessments check the website’s infrastructure, applications, and systems using automated technologies to look for known vulnerabilities. This involves performing network vulnerability scans, web application vulnerability scans, and port scans.
Penetration testing: Vulnerability assessments may include manual penetration testing and automated scans. Security experts replicate actual attacks to find flaws that automated methods might miss.
Analysis and reporting: The vulnerability assessment results are analyzed, and a detailed report is generated. The report typically includes a list of identified vulnerabilities, their severity, and recommendations for remediation.
A website’s compliance with specific security requirements, rules, or best practices is the main focus of security compliance audits. In order to preserve sensitive data and uphold customer trust, these audits are intended to ensure that businesses adhere to regulatory standards and industry best practices.
Typically, the process entails the following:
Site Audit Services
Mageplaza offers FREE site health check (15hrs) to help you identify any website flaws & weaknesses and fix them before they start costing you a fortune.
Explore More

Website security audit requires several crucial measures to be taken. The following seven steps will help you get through the procedure:
Use automated software or services to check the security of your website. These programs check the website for widespread vulnerabilities, including out-of-date software, configuration errors, weak passwords, or known security flaws. In their report, they identify potential weaknesses that demand more research.
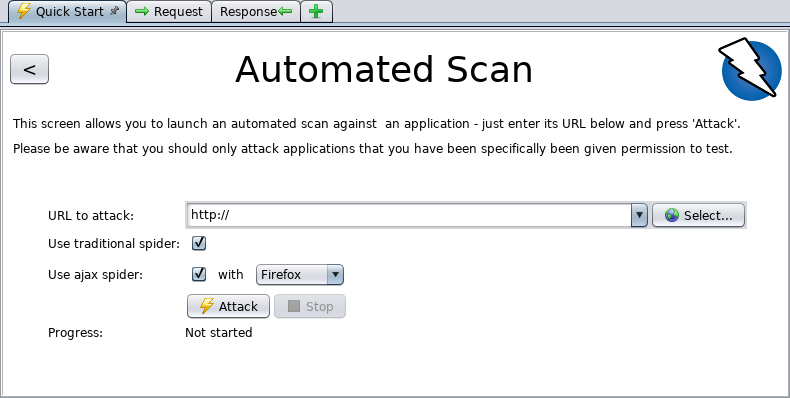
Configure the Scanner: Set up the scanner with your website’s details. Include URL endpoints, login credentials (for authenticated scans), and specific areas you want to focus on.
Run the Scan: Execute the scan during low-traffic periods to minimize impact on website performance. Ensure the scan covers both the frontend and backend components of the site. Review the Report: Analyze the scan results to identify detected vulnerabilities such as outdated software, configuration errors, weak passwords, and known security flaws.
Prioritize Issues: Based on the report, prioritize vulnerabilities for remediation, focusing first on those that pose the highest risk to your website’s security.
Settings for the website, such as the server configurations, file permissions, and directory structures, should be reviewed and analyzed. Make that the server configurations are safe and in line with industry standards.
To prevent unwanted access, check the permissions on files and directories. Search for insecure settings that can expose private data or make it easier for attackers to exploit weak points.
Analyze the access rights associated with each user account on your website. Decide which accounts need to be disabled or removed if they are inactive or useless. To ensure that access is restricted to only what is required, ensure user roles and permissions are properly given.
Audit User Accounts: Regularly review all user accounts on your website to identify and remove or disable any inactive or unnecessary accounts.
Assess Permissions: Carefully analyze and document the access rights for each account, ensuring that each user has only the permissions necessary for their role.
Update Access Controls: Adjust user roles and permissions as needed to tighten security and minimize the risk of unauthorized access.
Implement Multi-Factor Authentication (MFA): Require MFA for all users, adding an extra layer of security beyond just passwords.
Enforce Strong Password Policies: Mandate complex passwords that must be changed regularly, and encourage or enforce the use of password managers.
Regular Reviews: Schedule periodic reviews of user accounts and permissions to adapt to changes in your website’s usage or personnel.
Educate Users: Provide training or resources on the importance of security practices, including secure password creation and the handling of phishing attempts.
In order to prevent unwanted access, regularly conduct user access reviews. As a security measure, encourage the usage of multi-factor authentication and implement strong password policies.

Update the website’s software regularly, including the content management system (CMS), plugins, themes, and any other relevant elements. An attacker may be able to use known vulnerabilities in outdated software.
Apply security updates and patches as soon as software providers release them. To make sure you are utilizing the most recent, secure versions of all software components, often check for updates.
Defend the domain and IP address of your website from unauthorized access. To manage incoming and outgoing traffic, configure your firewall properly. Monitor network traffic and employ intrusion detection technologies to spot and stop hostile activity.
Configure Firewall: Properly set up your firewall to control and monitor both incoming and outgoing traffic to protect your domain and IP address.
Employ Intrusion Detection: Utilize intrusion detection systems (IDS) or services to continuously monitor network traffic for signs of malicious activity and potential threats. Regular DNS Reviews: Periodically check and update your DNS configurations to ensure they are secure and correctly direct traffic to your site.
Domain Registrar Settings: Regularly review your domain registrar settings for any unauthorized changes and ensure contact information is up-to-date and privacy settings are enabled if needed.
SSL Certificate Management: Verify that your SSL certificate is not only current but also properly installed and issued by a reputable authority to encrypt data transfers.
Access Controls: Limit access to your domain and hosting management settings to authorized personnel only, using strong authentication methods.
Regularly check the expiration dates of service agreements, subscriptions, or SSL certificates connected to your website. Create a renewal plan to ensure these services are renewed before they expire.
If they are not renewed, security safeguards may no longer be in place, and website operation may be affected. Keep track of renewal dates and set up reminders to prevent service interruptions.
Examine the traffic statistics on your website to look for any unusual or suspicious activity. Review security logs, error logs, and access logs frequently.
Look for any indications of potential security breaches, such as recurring access from suspect IP addresses, patterns of abnormal or excessive login attempts, or other indicators. You can take rapid action by monitoring website traffic using tools or services that send out real-time warnings for suspicious activity.
You may conduct a thorough website security audit by following these step-by-step instructions, and you can then put the vital security measures in place to shield your website from any threats. You can guarantee the security and integrity of your online presence by doing these audits regularly and being alert about website security.

This checklist provides a foundational framework for conducting thorough website security audits. Regularly reviewing and updating your security measures in line with this checklist can significantly enhance your website’s resilience against cyber threats.
Security Scanning:
Use automated tools for vulnerability scanning.
Analyze and prioritize findings.
User Accounts and Permissions:
Audit user accounts.
Adjust permissions.
Enable MFA.
Enforce strong passwords.
IP and Domain Security:
Configure firewalls.
Implement intrusion detection.
Review DNS and domain settings.
Maintain valid SSL certificates.
Software and Plugins:
Update all software and plugins.
Remove outdated components.
Web Application Firewall (WAF):
Check WAF configuration.
Update rules and settings.
Penetration Testing:
Conduct ethical hacking.
Remediate identified vulnerabilities.
Data Protection:
Encrypt sensitive data.
Regularly back up data.
Malware Monitoring:
Scan for malware.
Address detections promptly.
Security Policies:
Update security policies.
Educate team on security practices.
Compliance:
Ensure legal and regulatory compliance.
Document compliance actions.
This is an open-source web application security scanner developed by OWASP (Open Web Application Security Project). It’s designed to find security vulnerabilities in web applications during testing phases. ZAP is suitable for beginners and experienced testers, offering automated scanners as well as tools for manual testing.
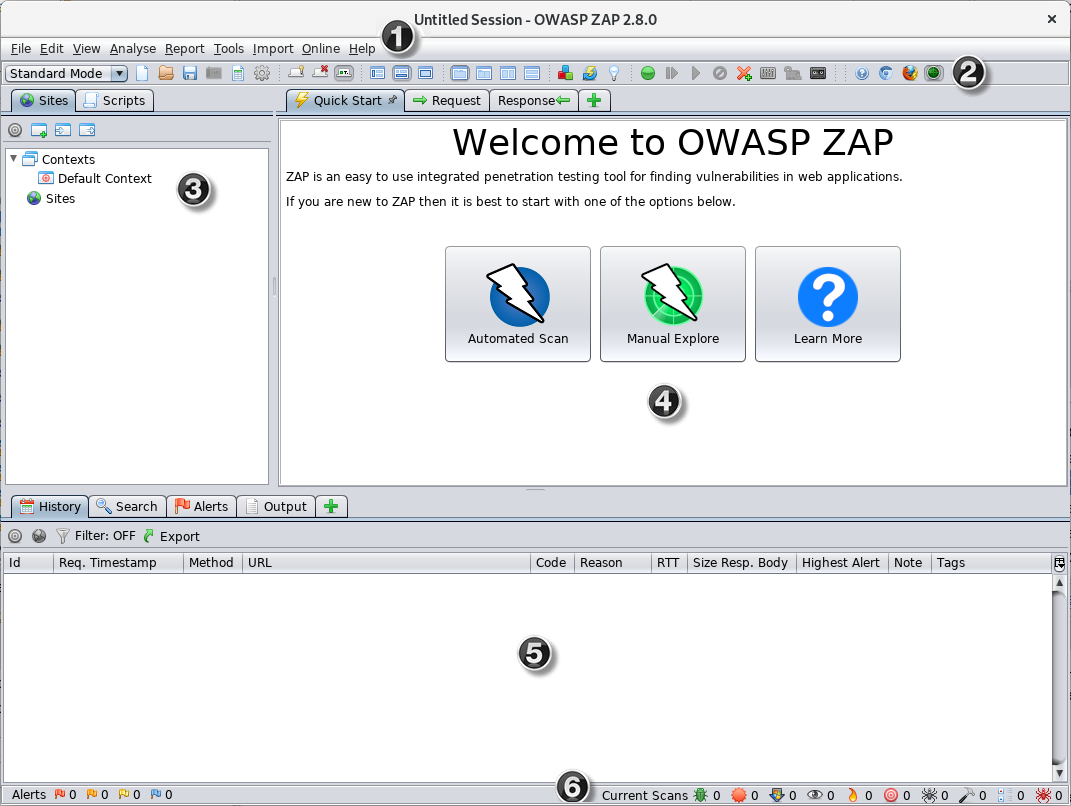
Main features:
Automated vulnerability scanning
Passive and active scanning modes
Spidering for content discovery
Support for various authentication methods
Extensive reporting capabilities
It’s a widely used proprietary vulnerability assessment tool for identifying vulnerabilities, misconfigurations, and security issues in various environments, including web applications. Nessus is known for its extensive plugin library that enables it to detect a wide range of issues based on known vulnerabilities.
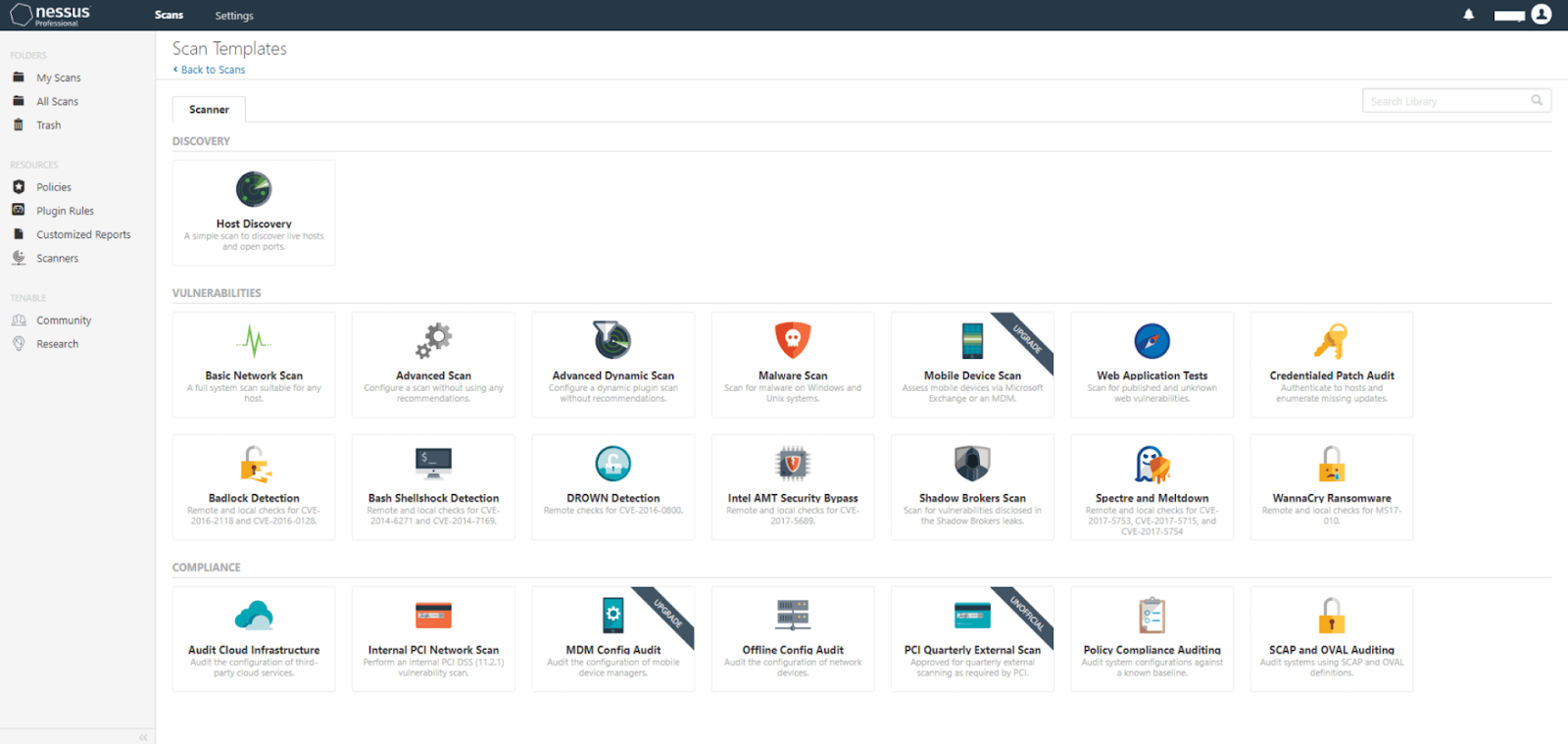
Main features:
High-speed discovery and configuration auditing
Asset profiling and sensitive data discovery
Vulnerability analysis with an extensive plugin library
Customizable reporting
A cloud-based service by Qualys that automates crawling and testing of web applications to identify vulnerabilities. It’s designed to scale and easily integrate with other Qualys tools for comprehensive security coverage.
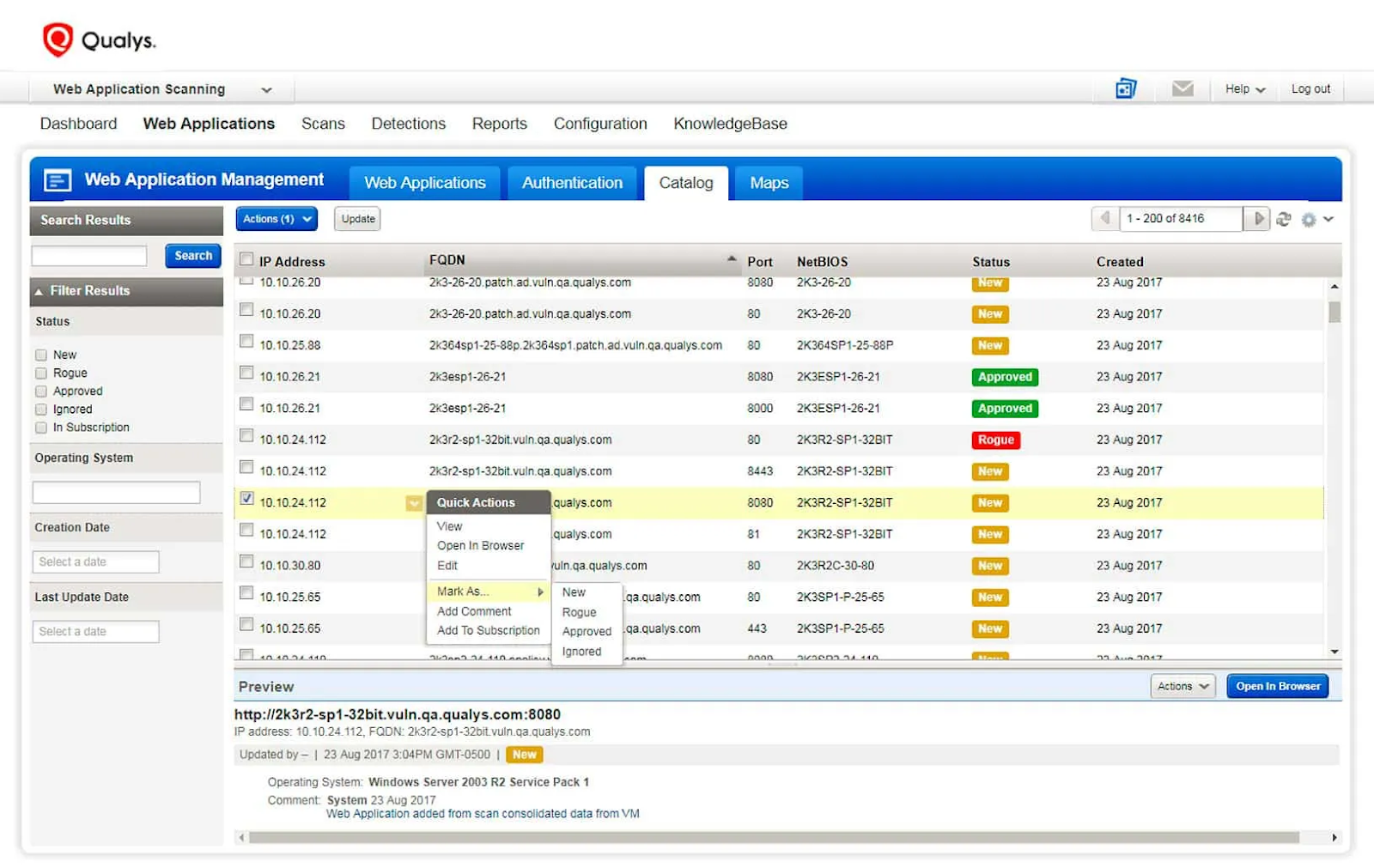
Main features:
Continuous security assessments
Detection of common and advanced vulnerabilities
Integration with CI/CD pipelines for DevSecOps
Detailed vulnerability management reporting
In conclusion, a website security audit is an essential step in ensuring your online presence is safeguarded. You may find vulnerabilities, repair security flaws, and protect your website from potential dangers by conducting a thorough audit.
You can evaluate your website’s security posture using various security audits, including network, application, and physical security audits. Your total security is further improved by considering social engineering audits, data security audits, and wireless security audits.
At Mageplaza, we understand the importance of website security and offer professional website security audit services. Our experienced experts can thoroughly assess your website, identify vulnerabilities, and provide actionable recommendations to enhance your security.
Visit our Site Audit Service to learn more about our comprehensive security solutions and schedule a consultation. With our Magento Site Audit Services, your website can:
Witness improvements in not only security & privacy but also SEO
Better performance and user experience
keep pace with Google Algorithm
Don’t wait until it’s too late. Safeguard your website today by leveraging our website security audit service.